Awareness and Training Domain
Hackers often target people rather than machines. Careless user actions put the confidentiality of sensitive data at risk. Awareness and Training ensure every person understands their role in keeping data safe. Leaders should set the rules by writing clear policies.
These documents explain who needs training and how often they must retrain. Every employee should attend "literacy" training. These lessons cover basic cybersecurity safety, such as spotting scams. Security teams should update training materials to adapt whenever new threats appear. This keeps the staff ready for the latest types of cyber attacks.
People with security roles should take specialized training focused on their responsibilities. Organizations should track training completions and maintain these records. When everyone knows the rules, these controls create a human firewall. Informed employees act as a strong shield for protecting Controlled Unclassified Information (CUI).
Policy Writing
Domain level policies address the controls implemented within systems and organizations. Policies are the perfect home to define control parameters, such as frequencies. Procedures describe the implementation of policies or controls. Organizations may document procedures within the system security plan or within separate documents. Here are some of the principles that guided this awareness and training policy:
- Restating controls does not constitute an organizational policy or procedure.
- Policies should omit references to specific technologies.
- Address procedures to the individual or role performing the task.
- Use plain language when writing procedures and avoid technical jargon.
Policy Structure
A cover page tracks specific details regarding the policy, including:
- Version - number capturing major and minor policy revisions
- Effective Date - date of policy dissemination
- Last Review Date - date the policy was last reviewed
- Next Scheduled Review Date - the date for the next mandatory policy evaluation
- Classification - internal categorization of the policy’s sensitivity for confidentiality
NIST SP 800-53 defines specific objectives for domain-level policies. From this guidance we incorporate the following major sections into our policy:
The purpose statement should identify why the policy exists and what it aims to achieve.
The scope should identify who it applies to and under what circumstances.
The policy governance section covers most of the organization defined parameters. These subsections cover the following details:
- Policy Dissemination List - defines roles or personnel to disseminate the policy
- Procedure Dissemination List - defines roles or personnel to disseminate the procedures
- Policy Level - organization-level; mission/business process-level; system-level
- Policy Owner - defines an official to management the policy and supporting procedures
- Policy Review Frequency - how often the organization reviews and updates the policy
- Policy Review Triggers - events that require an out-of-cycle policy review or update
- Procedure Review Frequency - how often the organization reviews and updates the procedures
- Procedure Review Triggers - events that require an out-of-cycle procedure review or update
The fourth section includes our policy statements. Subsection headings group related Policy statements together. Each policy statement has a unique number for traceability to other documents. A policy statement number consists of the section, subsection, and policy statement order.
The fifth section identifies the relevant roles and responsibilities identified in the policy. A single, short paragraph describes the responsibilities for each role. The sixth section identifies the supporting procedures. We opted to align our subsection headings with the names of supporting procedures. The seventh section identifies related documents, to include relevant policies. The eighth section documents a revision history. This table captures policy changes, including: version, effective date, approver(s), change summaries. The ninth section captures a formal authorization of the policy by the policy owner.
Policy Statements
NIST identified a named set of procedures for each practice within NIST SP 800-171. The assessment guide (SP 800-171A) contains the original mappings. The CMMC assessment guides include this mapping as well. NIST derived these assessment objects from SP 800-53A. Table D maps SP 800-171 security requirements to controls from SP 800-53. For this domain, we followed the original procedures defined for the underlying controls.
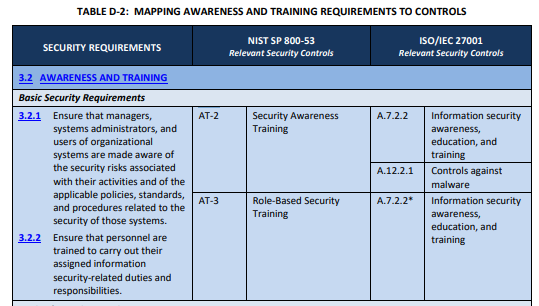
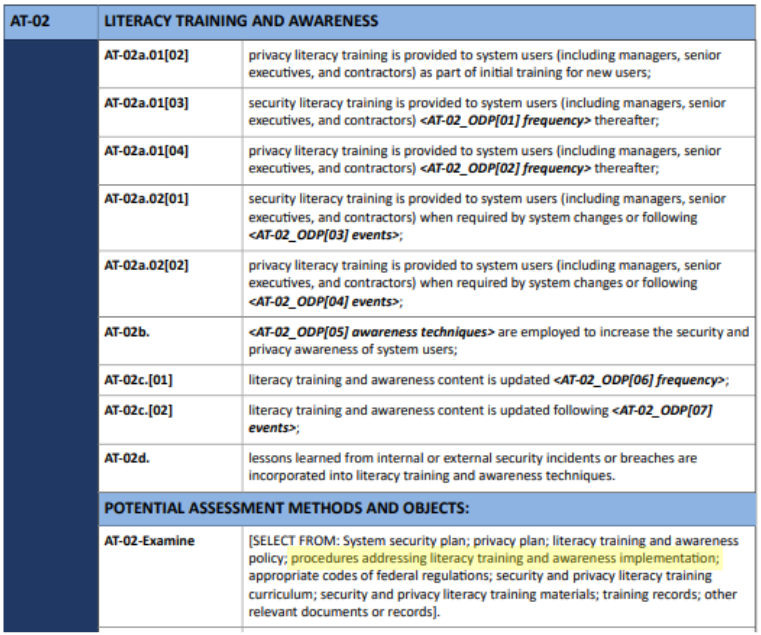
Literacy Training and Awareness Implementation
This section outlines how organizations train personnel to protect Controlled Unclassified Information (CUI). All users attend security training when they start their jobs and every year after. These lessons cover CUI handling, password safety, and physical security. High-risk staff, such as leaders and accountants, receive training to spot email scams. All users learn to identify and report security issues and Insider Threats. An Acceptable Use Policy (AUP) teaches staff how to protect CUI according to federal laws.
CMMC Objectives Covered in This Section:
- (2) objectives from AC.L2-3.1.3
- (1) objective from AT.L2-3.2.1
- (2) objectives from AT.L2-3.2.3
- (1) objective from IR.L2-3.6.1
Security Training Implementation
This section describes specialized training for staff with specific security duties. The organization maintains a list of roles to provide tailored technical training. Roles posting on public websites must complete training to prevent unauthorized disclosures. Incident response roles complete annual training to detect, analyze, and stop attacks. Employees monitoring system logs receive training on the logging tools used. Staff receive updated training when a role changes or new cyber threats emerge. Specialized lessons ensure that technical experts have the skills to protect the system.
CMMC Objectives Covered in This Section:
- (1) objective from AC.L2-3.1.22
- (1) objective from AT.L2-3.2.1
- (3) objectives from AT.L2-3.2.2
- (1) objective from AU.L2-3.3.4
- (1) objective from CM.L2-3.4.5
Security Training Records
This section describes how the organization tracks and saves training records. A compliance matrix tracks the status of all required lessons. Staff review this every three months to remediate overdue training assignments. The organization keeps training completion records for six years. These saved records prove historical compliance and support official audits. By maintaining these files, the organization ensures it meets all federal documentation standards.
CMMC Objectives Covered in This Section:
- (1) objective from AT.L2-3.2.1
- (1) objective from AT.L2-3.2.2
- (1) objective from AT.L2-3.2.3
Syncing Policies with System Security Plan
FedRAMP guidance on how to write a control implementation statement states the following:
- Implementation statements should reference supporting policies and procedures.
- If a document is long, point to the exact sections that matter instead of the whole thing.
- Write summaries so that reviewers don't have to go look up other documents.
Write your policies before you start drafting your security plan. K2 GRC shows you exactly how each part of your policy connects to your security goals.
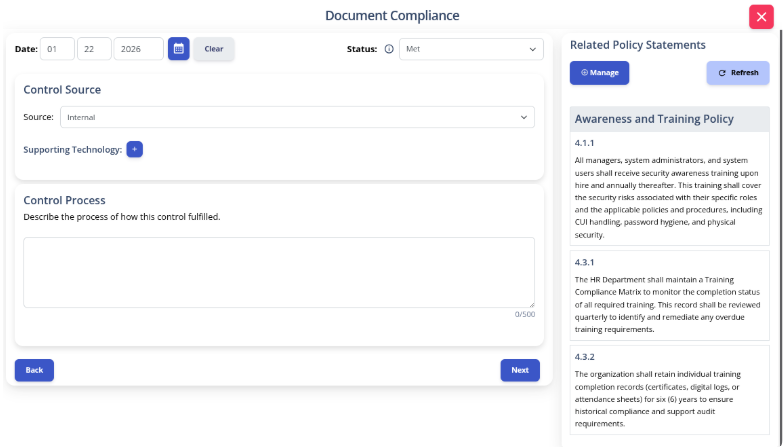
The input screen shows the specific policy rule and its ID number. This identifies relevant policy statements when writing your system security plan implementation statements. The system then adds your work to the final security plan template.
Deliver and Track Training using eLearning
K2 GRC also delivers and tracks policy attestations and eLearning training modules. A centralized policy repository enables organizations to define a dissemination list for policies. Only authorized roles or individuals may access policies relevant to them. K2 GRC can also distribute policies and document acknowledgements from users. These tasks can relate back to controls to document compliance with regulatory requirements.
K2 GRC has a library of over 500 existing training modules. As our eLearning platform continues to grow, we now support custom content creation. The custom module creator allows organizations to create and deliver their own training. Custom content may include SCORM, common document formats (PDF, PPT, etc), or videos. Administrators can create a question bank using multiple-choice, short-answer, or true-false. An answer key can score responses, enabling the establishment of a pass-fail threshold.
In some cases, organizations may leverage public training provided by other authorities. An example is the CDSE training provided by DOD for Controlled Unclassified Information. The custom module creator can embed this training and track user completions. Users may upload their certificates from CDSE to document successful training completion. Organizations may also create their own question bank to score content comprehension.
Conclusion
Hackers often target people to bypass technical controls. The Awareness and Training domain establishes strong defenses for a system's human elements. Organizations must define rules by writing and communicating clear policies. They should provide literacy and insider threat training to every user. They should deliver focused training for employees at higher risk. Establishing and communicating an Acceptable Use Policy memorializes the rules of behavior. Organizations should provide specialized training to technical roles specific to their responsibilities. They should update training and policies in response to new threats. They should monitor training progress to resolve overdue assignments. They should establish record keeping guidelines for training records for auditing and assurance. K2 GRC can simplify training distribution, tracking, and documentation.

%201.png)
%201.png)

