Ransomware Risk Assessment: Quantifying The Most Impactful Controls
🔐 What’s This Blog About?
This blog explains how to combine MITRE ATT&CK, NIST SP 800-53, NIST CSF 2.0, and FAIR to quantify ransomware risk in financial terms. It shows how organizations can map ransomware techniques to security controls, measure gaps, and translate technical weaknesses into clear dollar-based risk insights for leadership.
Key Takeaways
- ✅ Map ransomware attack techniques (MITRE) to security controls (NIST) to identify real mitigation gaps.
- ✅ Use NIST CSF functions (Protect, Detect, Respond, Recover) to understand how controls reduce likelihood and impact.
- ✅ Apply the FAIR model to convert technical risk into annualized loss exposure (ALE), probable loss ranges, and tail risk.
- ✅ Foundational controls like System Monitoring (SI-4), Configuration Management (CM-6), and Access Controls (AC-2, AC-3, AC-6
Google expects ransomware to remain a top problem for internet security in 2026. Security architects can use any number of frameworks to build their defenses, including:
- MITRE ATT&CK: Maps out how hackers attack.
- NIST SP 800-53: Provides the library of security controls to stop them.
- NIST CSF 2.0: Organizes those controls into defensive goals (like Protect and Detect).
- FAIR: Calculates the financial value of that risk.
When used together, practitioners can rank controls by their effectiveness against a threat. MITRE ATT&CK and NIST SP 800-53 provide a common language for describing threats and controls. Research from MITRE Engenuity bridges the two to create a potential mitigation benchmark. By assessing implementation gaps, organizations can derive a tangible vulnerability score. The NIST CSF organizes controls by function, enabling alignment with FAIR risk factors. The final output is business-oriented, translating technical risk into dollars and probabilities.
Ransomware Threat
If you know neither the enemy nor yourself, you will succumb in every battle. - Sun Tzu
Sophos surveyed 5,000 organizations in 14 countries for its latest ransomware report. They reported that ransomware hit 59% of organizations last year.
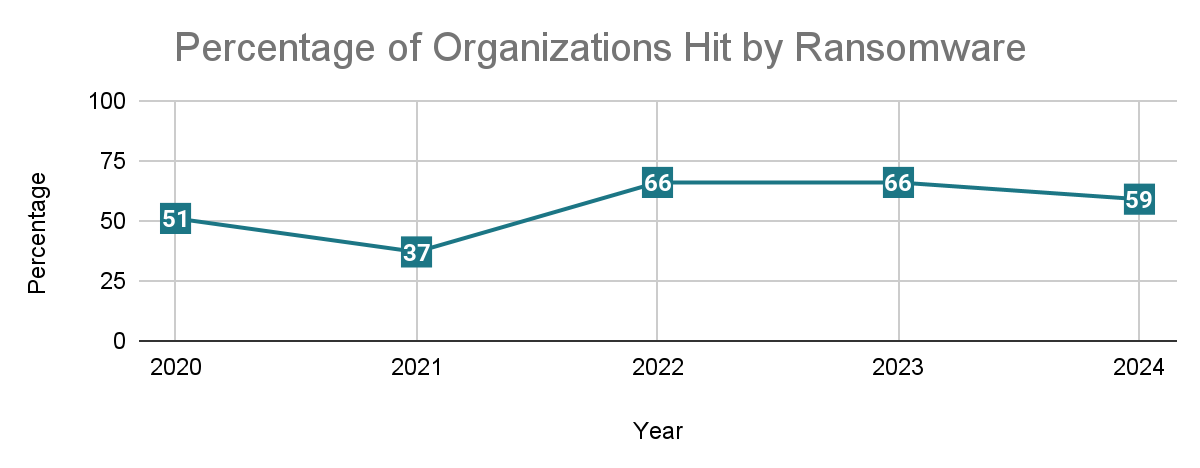
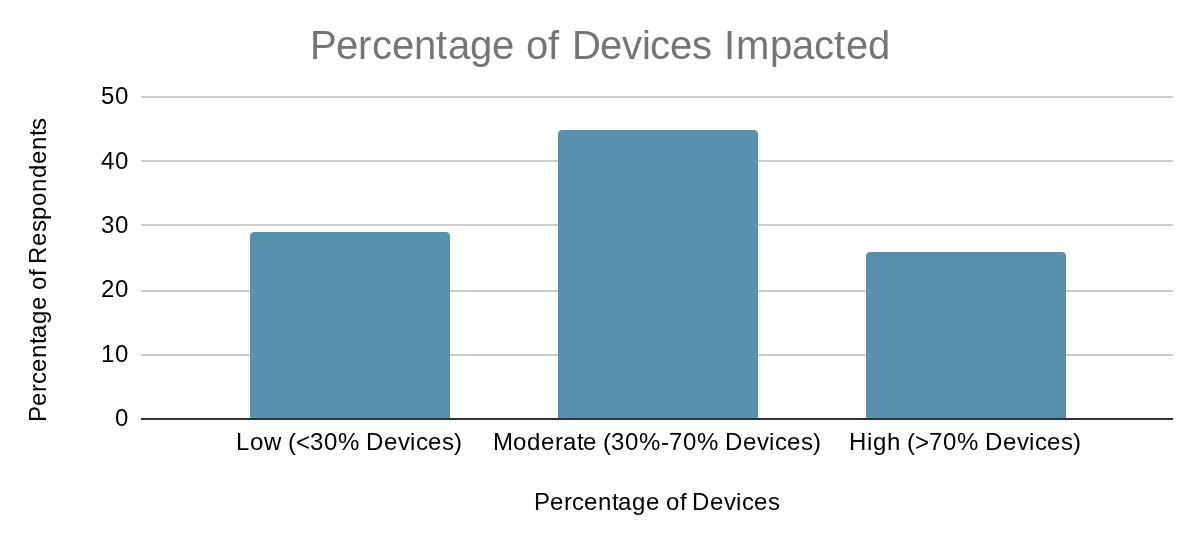
Most respondents reported ransomware's impact affected a moderate percentage of their devices. Less than 5 percent reported that ransomware affected more than 90% of their devices.
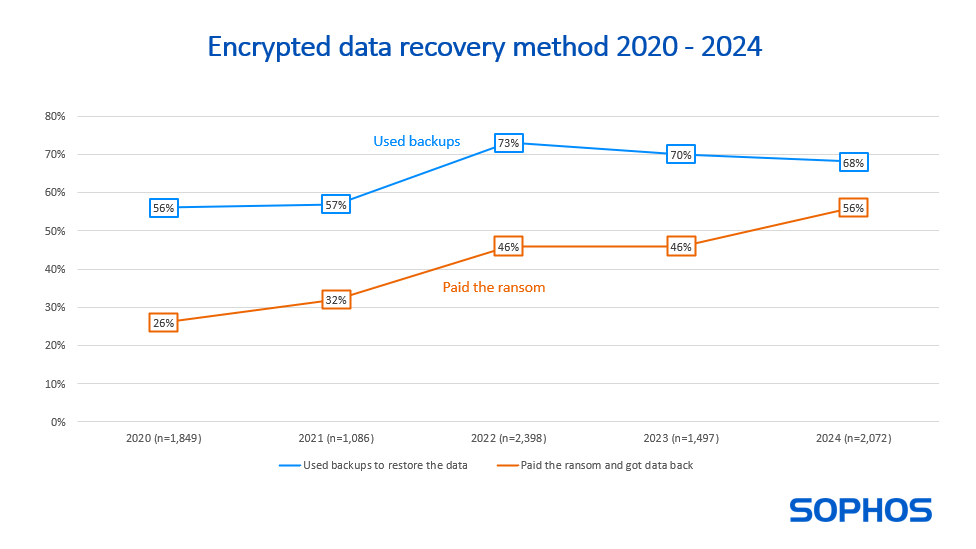
Although the percentage of affected organizations decreased, recovery costs have increased 50%. The average recovery cost was $2.73M and more than half of affected organizations paid the ransom.
Several cybersecurity research reports have identified relevant techniques used during ransomware attacks. From these publications, we included the following into our risk assessment:
- T1133 - External Remote Services (Arctic Wolf, Madiant)
- T1078 - Valid Accounts (Arctic Wolf, Madiant, Trustwave)
- T1566 - Phishing (CISA, Madiant, Trustwave)
- T1059 - Command Scripting Interpreter (CISA, Artic Wolf, Madiant, Trustwave)
- T1003 - OS Credential Dumping (CISA, Arctic Wolf, Madiant, Trustwave)
- T1530 - Data from Cloud Storage (Madiant)
- T1219 - Remote Access Tools (CISA, Arctic Wolf)
- T1490 - Inhibit System Recovery (CISA, Madiant)
- T1567 - Exfiltration over Web Service (CISA, Madiant, Trustwave)
Mitigating Controls
The MITRE Center for Threat Informed Defense (CTID) maps SP 800-53 controls to MITRE ATT&CK. From this source we derived a set of base controls relative to the ransomware techniques.
The MITRE CTID mapping only maps techniques to base controls. We extended the mappings to enhancements for the three SP 800-53 security baselines. This allows practitioners to see all relevant controls and enhancements for each baseline.
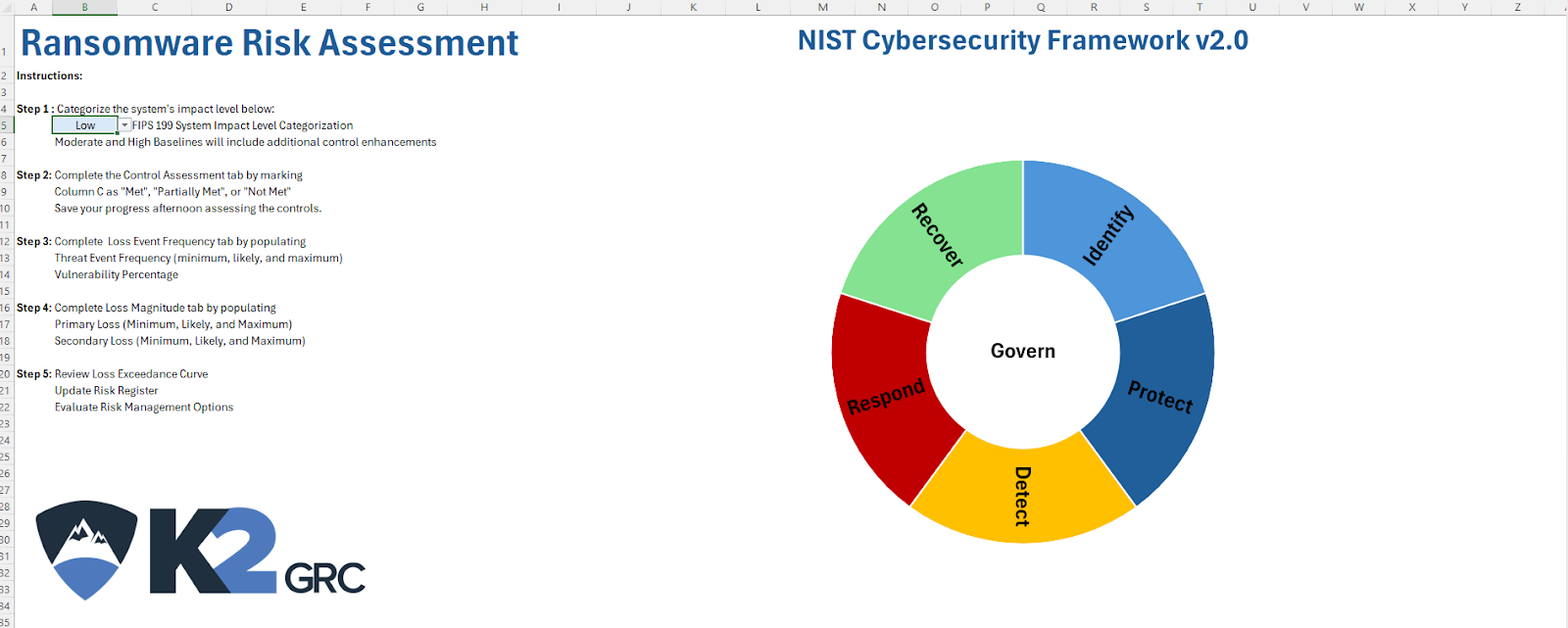
Defining Mitigations
Neither NIST SP 800-53 nor MITRE CTID define the nature of how a control mitigates a technique. The NIST CSF 2.0 categorizes controls based on six defensive outcomes:
- Govern (GV) – The organization establishes cybersecurity risk management strategy, expectations, and policy.
- Identify (ID) – The organization understands its current cybersecurity risks.
- Protect (PR) – The organization uses safeguards to manage cybersecurity risk.
- Detect (DE) – The organization finds and analyzes possible cybersecurity attacks and compromises.
- Respond (RS) – The organization takes action to a detected cybersecurity incident.
- Recover (RC) – The organization restores assets and operations affected by a cybersecurity incident.
NIST has categorized SP 800-53 controls into one or more CSF functions. These functions characterize the mitigation capabilities of each control. Within the risk assessment workbook, an assessment tab populates with the relevant controls. Practitioners must assess a status using standardized inputs (e.g. Met or Not Met).
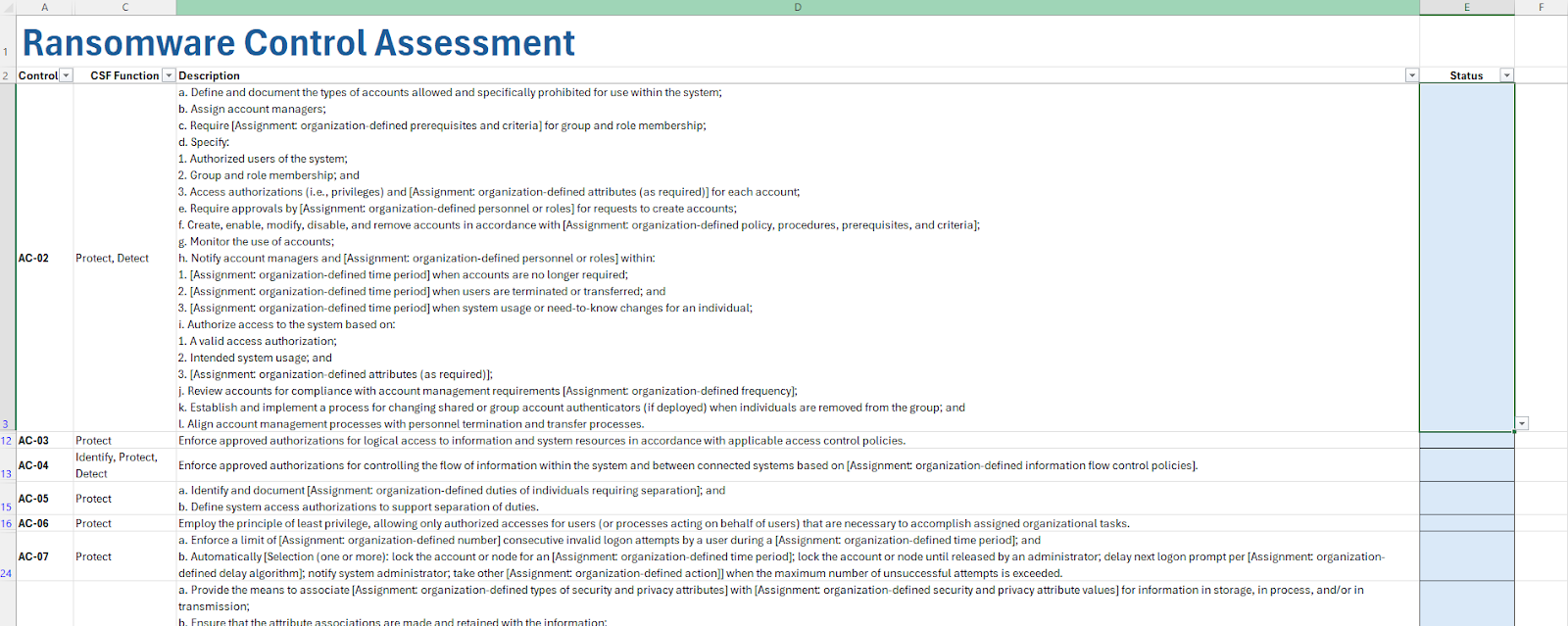
FAIR Model
The Factor Analysis of Information Risk (FAIR) model looks at two primary factors of risk:
- Loss Event Frequency (LEF) - how often the threat will create a loss event
- Loss Magnitude (LM) - the primary and secondary impacts of a loss event
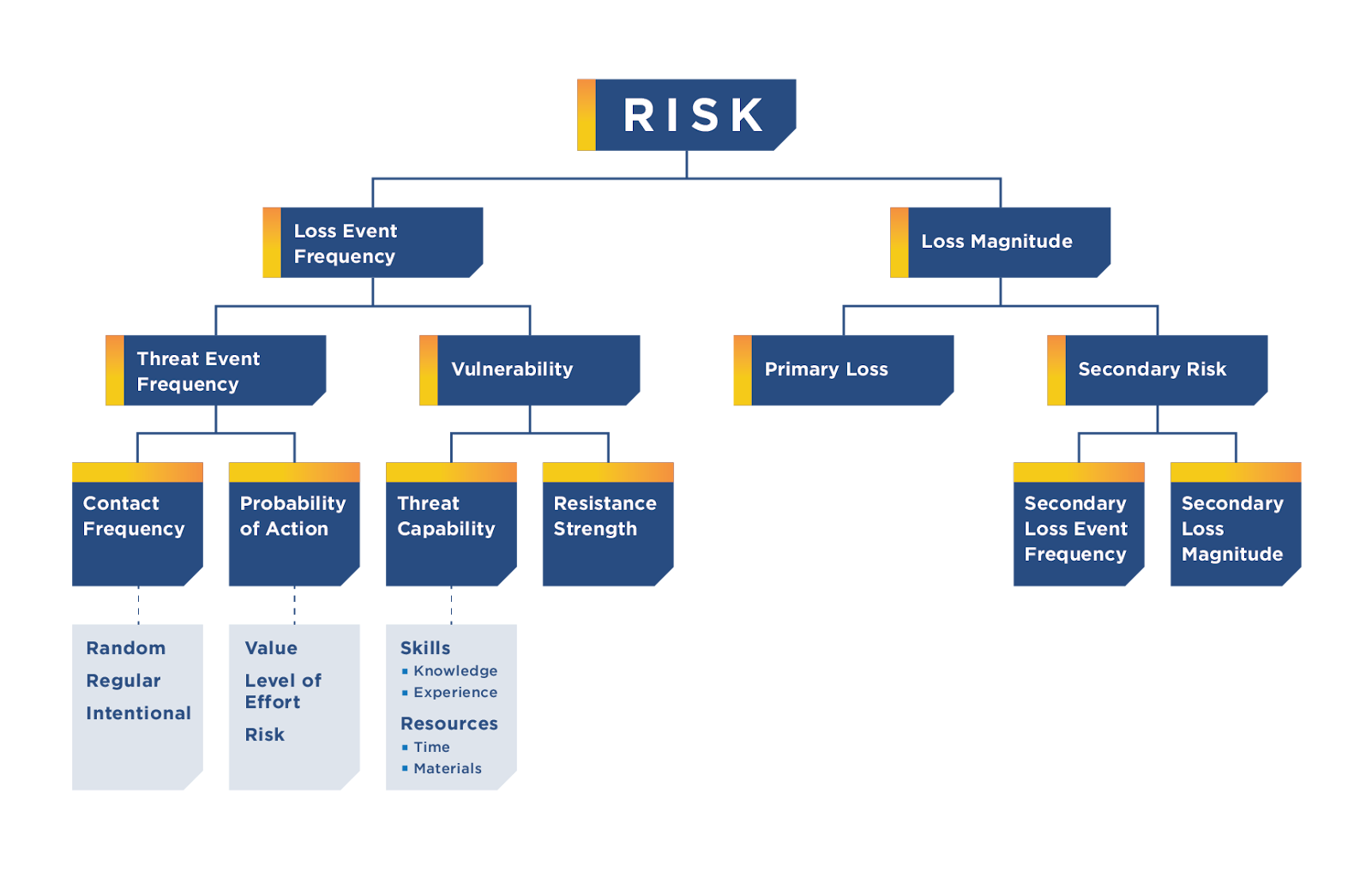
Loss Event Frequency (LEF)
The number of times a threat occurs and a vulnerability percentage determine the LEF. Threat intelligence can inform how often an organization might face a ransomware threat. The status of relevant mitigating controls can inform the vulnerability percentage.
Not all mitigating controls affect the vulnerability percentage. The most important controls are those that provide protection against the threat. The NIST CSF 2.0 defines this category of control within the Protect function. Controls within the Identify function act as a deflation coefficient. Protect controls are only effective against the percentage of assets identified. Governance controls act as the sustainability mechanism for protection controls. Governance policies, oversight, and resource allocation prevent the operational decay of protective controls.
Protective controls received a .50 weighting factor for each related MITRE technique. Governing and identifying controls received a .25 weighting factor. These coefficients were not aggregated within a single technique. If a control has protect and identify functions, it only receives the protect weight. The model aggregates control coefficients for each technique relative to a tactic.
There are four inputs into the LEF calculation. The number of times the organization will face a ransomware threat has three inputs. These inputs account for uncertainty in the estimated annual rate of occurrence. The final input is the vulnerability percentage. The workbook calculates an informative vulnerability percentage based on assessment inputs. The practitioner can reference this output when assessing the vulnerability percentage.
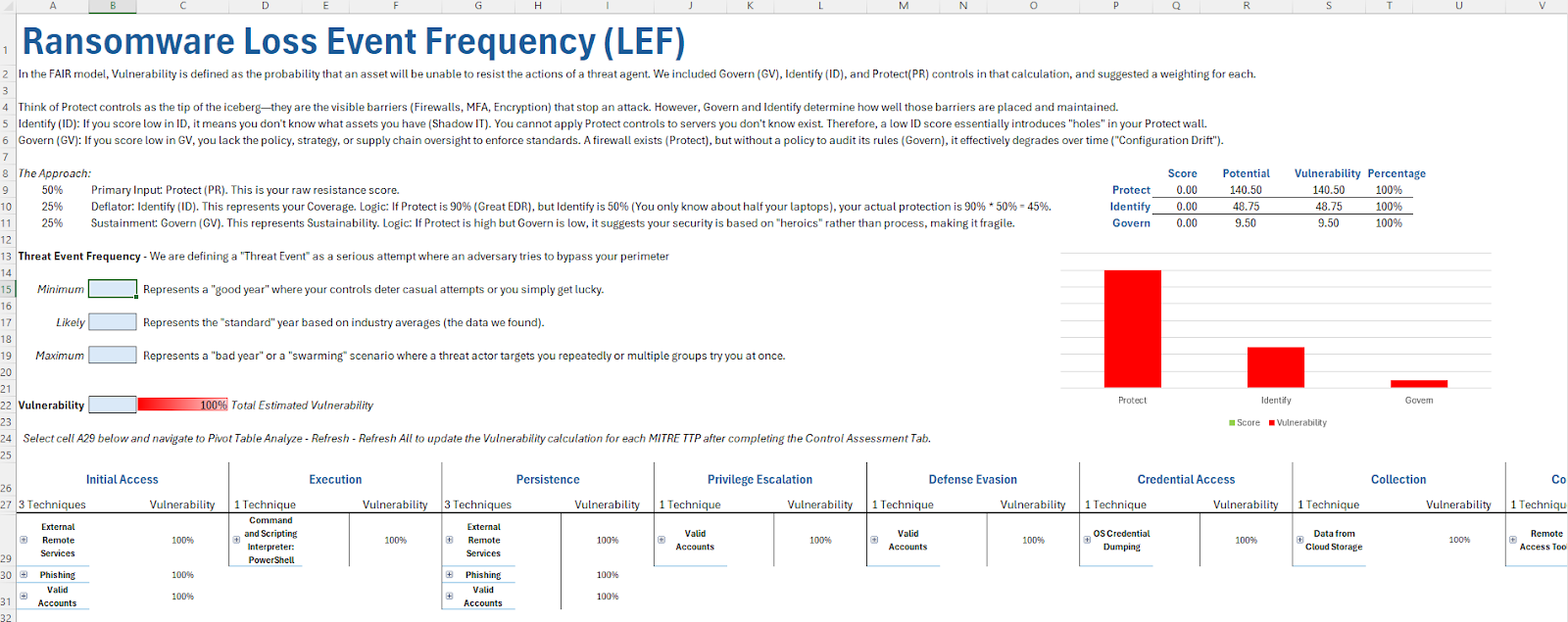
Loss Magnitude (LM)
The detect, respond, and recover functions of the CSF mitigate the loss magnitude. Respond controls act as the containment mechanism, governing the speed of reaction. They arrest the propagation of a threat and truncate the accumulation of costs over time. Detect controls serve as the prerequisite trigger for respond controls. Their effectiveness determines the Mean Time to Detect (MTTD) an adversary action.
The MITRE CITD mapping does not include response controls, which have broader applicability. To fill this gap, we incorporated base controls from SP 800-53 with a mapping to the respond function. This extended relationships into control enhancements from the three SP 800-53 baselines.
Not all techniques are relevant for Loss Magnitude. Relevant techniques included only those related to execution, exfiltration, and impact tactics. Response controls received a .50 weighting factor for each related MITRE technique. Detect and recover controls received a .30 and .20 weighting factor.
There are six inputs into the Loss Magnitude calculation. The practitioner estimates low, moderate, and high primary and secondary loss estimates. The assessment of mitigating controls informs these estimates input by the practitioner.
Image Source: Ransomware Risk Assessment
Loss Exceedance Curve (LEC)
The risk assessment inputs plot a loss exceedance curve (LEC). The LEC uses a 1,000 year Monte Carlo simulation and plots the probability of a given loss. This data enables the practitioner to identify:
- Reasonable loss - loss with 90 percent probability
- The Annualized Loss Exposure (ALE) - the average of all scenarios.
- The Median Loss - loss with a 50 percent probability.
- The Tail Risk - loss with a 10 percent probability.
Risk Register
The risk register includes four sections describing the assessed risk. These sections include risk identification, FAIR outputs, control posture, and risk management.
Risk Identification
A risk register should have a unique identifier and scenario name for each risk. The workbook names an adversary based on the tailoring selection of SP 800-53. The workbook also lists relevant MITRE techniques included in the assessment.
FAIR Outputs
An average of the Monte Carlo simulation determines the annualized loss exposure (ALE) . Tail Risk represents the financial threshold with a 10% probability in a given year. Single loss expectancy (SLE) is the sum of primary and second loss averages. An average of the Monte Carlo simulation determines the less expectancy frequency (LEF).
Control Posture
Protect, govern, and identify control scores divided by their potential equals prevention resistance. Vulnerability gap is the inverse of prevention resistance. Respond, detect, and recover control scores divided by their potential equals mitigation resistance. Ranking the sum of vulnerability gap scores identifies the top failing controls.
Risk Management
Practitioners should assign risks within the register to an owner. The owner selects a treatment strategy by accepting, mitigating, transferring, or avoiding. Should a risk owner decide to mitigate a risk, they can link an action plan and specify a residual risk target.
Top Ransomware Controls
Using this method, we quantified the impact of all ransomware ‘mitigating’ controls. Five controls represent 20% and 15% of the potential protection and detection scores. Stack ranking the mitigating value revealed the following as most impactful:
SI-4: System Monitoring
This control acts as the "eyes and ears" of your infrastructure. It requires continuous monitoring to detect indicators of compromise (IoCs) in real-time. Organizations can use tools like EDR, SIEM, or IDS to analyze network traffic and system logs. These tools find anomalies, identifying the "smoke" before the fire of encryption begins.
NIST categorizes SI-4 in the identify, detect, and protect functions of the CSF. The protect categorization of SI-4 relative to 14 techniques within the LEF produced a score of 7.0 (.5 each). The detect categorization of SI-4 relative to 3 techniques within the LM produced a score of .9 (.3 each). This control received a potential score of 7.9.
CM-6: Configuration Settings
This control represents the "hardening" of your environment. It ensures system configurations use security benchmarks to reduce the attack surface. This includes disabling unnecessary services, closing unused ports, and changing default passwords. By locking down the baseline configuration, you remove vulnerabilities ransomware scanners look for.
NIST categorizes CM-6 in the protect and detect functions of the CSF. The only technique not mitigated by CM-6 was T1567 Exfiltration Over Web Services. The protect categorization of CM-6 relative to 13 techniques within the LEF produced a score of 6.5 (.5 each). The detect categorization of CM-6 relative to 2 techniques within the LM produced a score of .6 (.3 each). This control received a potential score of 7.1.
AC-3: Access Enforcement
This control is the specific "gatekeeper" mechanism, enforcing who can access what. This prevents users (or attackers hijacking a user) from accessing restricted data. This relies on Access Control Lists (ACLs) and permissions to halt lateral movement.
NIST categorizes AC-3 in the protect function of the CSF. The only technique not mitigated by CM-6 was T1566 Phishing. The protect function of AC-3 relative to 12 techniques within the LEF produced a score of 6.0 (.5 each).
AC-6: Least Privilege
This control minimizes the damage a single compromised account can do. Every user and process should operate with only the least level of access necessary. This means removing "Local Administrator" rights from standard workstations. Malware cannot install itself if the user lacks required privileges.
NIST categorizes AC-6 in the protect function of the CSF. AC-6 does not mitigate T1566 Phishing and T1219 Remote Access Tools. The protect function of AC-6 relative to 11 techniques within the LEF produced a score of 5.5 (.5 each).
AC-2: Account Management
This control manages the "roster" of authorized accounts on the network. It ensures that only authorized, active personnel have valid credentials. This covers the process of creating, auditing, and disabling accounts. It prevents "zombie" accounts from lingering in the system.
NIST categorizes AC-2 in the protect and detect functions of the CSF. AC-2 mitigates five different ransomware techniques. The protect function of AC-2 relative to 8 techniques within the LEF produced a score of 4.0 (.5 each). The detect function of AC-2 relative to 2 techniques within the LM produced a score of .6 (.3 each). This control received a potential score of 4.6.
Conclusion
Combining MITRE, NIST, and FAIR transforms ransomware defense into a data-driven science. Mapping adversarial attacks to defensive capabilities establishes the bar for potential mitigations. Filtering their financial impact, enables translation of technical risk treatments to business leaders. Organizations don't need the newest, most expensive technology for an effective ransomware defense. As our quantification highlights, foundational hygiene controls provide the highest return on investment. This integrated approach empowers leaders to make decisions based on quantifiable risk exposure.

%201.png)
%201.png)

